Lire cet article en Français ![]()
Business Objects Security:
The 5 key questions you need to answer

Over the past few years, I have been working with hundreds of customers using 360Suite’ solutions for Business Objects. A common issue with most deployments is how Business Objects Security, with a capital “S”, is perceived whether it is by IT, QA, CISO or any person in an organization. Typically models are extremely complex, they lack common sense, and implementers have a poor understanding of regulations. Security needs to provide answers to the “W” questions: Who, When, What, Why and Where.
Security in an organization is more than ‘Who has access to what’. Business Objects Security can also be related to:
- Who had access to what? What permissions have changed and when?
- Who accessed what? Based on user activity…
- What changed in my platform?
- Are we complying with regulatory requirements?
- Can I protect my data outside of the platform?
Business Objects Security: Who has access to what?
Who has access to what? Easy to ask, tough to answer!
I had the chance to work with banks, federal entities, and Fortune 500 companies. An honest answer to this simple question is, “I do not know”.
Security models need to be as simple as possible working from a Role or Group and avoid individual user security. Most of the time, security rights are poorly implemented without understanding the needs of the security’s life cycle management. Over time, organizations forget exactly what was granted to specific users and the impact on the environments.
The best way to secure a deployment is to apply security at the database level, using row-level security. Additional security can be applied at the reporting level.
Current State in Business Objects: It is easy to find explicit rights. The issue when you assign security is that it impacts the entire environment like a domino effect. Each time you make a change, it can create downstream effects and by the end of it all, all you have is a maze.
The most common way to keep track of such changes for the best deployments is to follow changes on an Excel file, with the X-axis being the resources to be secured and the Y-axis being the users and user groups to be secured. This is pretty easy to do in a deployment of 10 users, but when you start to reach 100 or more users it becomes very tricky to keep track of everything since there are so many changes. People who change security come and go throughout the life of any organization.
Ask an admin: “What does user Bob have access to in detail?”, and the honest answer would be “I don’t know”.
Ask the CIO who has access to “Finance folders” with all the detailed security, and the honest answer would be “I don’t know” or “let me refer to an old Excel file”. Nowadays when security and data protection is crucial, this answer is no longer acceptable.
360Suite Solutions: 360Suite provides a real-time view of your Business Objects Security, and offers the possibility to document it via an Excel export which is not possible to do natively in Business Objects. You also have the possibility to make changes to the security and see all the impacted rights (inheritance and double inheritance).
Our solutions offer the possibility to display a user-centric and resource-centric view to audit your security in place and answer any questions.
Screenshot from 360Suite: Business Objects Security Management in a Live Security Matrix
Business Objects Security: Who had access to what?
Who had access to what? A common answer to that is “I don’t know” and “I do not know what the security changes were”.
Last year while working with a large East Coast Hospital regulated by HIPAA, they had an urgent need to know who had access to a specific folder six months earlier. The reality was that they could only guess and furthermore had no idea of any security changes.
Current State in Business Objects: Currently, the only answer to this question is to rollback to a previous backup. Once this is done, you can determine the explicit rights. No information is available about the life cycle management of the security changes for that specific resource.
360Suite Solutions: 360Suite is able to take daily snapshots of the security and compare changes over time like a time machine.
Business Objects Security : Who accessed what?
Imagine a situation where your company is facing a Data Leak. Financial information has been revealed online, and the source is most likely a WebI document. You’re able to map out your current Business Objects Security, and also retrieve the security model that was in place at a specific time. You can answer some questions such as the document was in that folder, and then it was moved to that folder where it is today. So you could say approximately 50 users between last year and today had potentially the right to access that document. Wow, that’s it?
Inevitably, you’ll be asked to reduce that list to the user who got their hands on it. Said differently, you will need to know who accessed these documents.
Current State in Business Objects: Specific permissions can be assigned to roles such that users assigned to these roles can only perform the specific actions on the corresponding objects. Although you control the scope of the records which the role can access, the complexity of the security model doesn’t preclude a mistake or an oversight from being made. Perhaps the custom access level was poorly defined and contains incorrect permissions. Perhaps best practices were not followed and granular rights were assigned on content. Perhaps inheritance was broken or conflicting permissions were granted. Shortcuts taken by (IT) support teams make identifying problems in the security model implementation difficult to monitor and difficult to fix as soon as possible.
360Suite Solutions: 360Suite provides an audit of resource-based activity so you can review effective and detailed permissions set for given groups and users for all the available Business Objects content types (public folders, user folders, inboxes, categories, etc). 360Suite also allows you to perform a more in-depth audit of user actions on resources, so you can find out the exact user account who performed a specific type of action on a particular resource on a particular day. In this manner, suspicious activity can easily be tracked and remedied quickly.
Mastering permissions is a big part of the Business Objects Security Management. Nonetheless, the security is not limited to permission management and auditing.
Business Objects Security Changes – Users’ Life Cycle Management
How do you know if a user who left the organization still has rights? Or if a user who moved to a new department does not have access to their old resources?
Current State in Business Objects: Explicit permissions can be found and administrators need to go fishing (and be lucky enough) to determine what the inherited and double inherited permissions are. By default, if a user is deleted and they own documents or instances, they are reassigned to the Administrator.
360Suite solutions: When a user leaves an organization or changes roles, 360Suite offers the “Owner Update” feature. You enter the name of the old user and the new user, and the object ownership is transferred from one to the other in just 3 clicks!
When a user leaves an organization, they are typically disconnected from the organization directory and the link between the organization directory and Business Objects is lost. However, the user (if an Enterprise alias has been created which is a best practice) still exists in Business Objects, typically without any granted access. 360Suite finds all these unlinked users and provides a way to remove them easily.
Account Recertification for Regulatory Compliance
Large organizations and federal organizations need to perform such recertification on a regular basis depending on their regulatory requirements. Some organizations do annual account recertification and then perform quarterly recertification based on predefined % of user’ accounts.
I had the chance to work with some of them and I can say that in 90% of the cases their account recertification was inaccurate. Typically, the main reasons were a mix of a poor understanding of account recertification rules, poor training of people implementing recertification, poor understanding of IT architecture from policymakers and an overall inability to have access to detailed information.
Are user accounts still needed and accurate? How would you proceed?
Current State in Business Objects: There are no acceptable native solutions available in Business Objects.
360Suite Solutions: This is a multiple-step process involving Users/Resources/Security.
First, you need to determine whether user access is still needed, this is based on an organization’s policy. Next, you need to have access and document security at the deepest level, then compare it to the policy in place.
Another step based on the activity or non-activity level is that 360Suite is able to capture, report and fine-tune recertification and trigger whether a specific user needs to be recertified or not.
With regards to unlinked users and groups, 360Suite is also able to find and clean up such unlinked actors.
Document Lifecycle and Traceability
All regulated industries need to be able to answer: Who changed what? When? In which document? With also the ability to see changes.
In most organizations, you have multiple report developers working on the same report. For example, when you work on a Microsoft Word document, you forward it to co-workers who make changes, and in the end, you have so many versions you have no idea what the proper version is, the visibility of who changed what, and what was changed. To some extent, you need to enforce a development policy in order to have a clear view of your documents’ lifecycle.
Current state in Business Objects: Limited version management is possible out of the box but does not comply with most regulations.
360Suite Solutions: 360Suite offers the possibility to Check-in and Check-out to a report. While a report is checked out, only the developer who checked it out can make changes (the Administrator can unlock if necessary). When reports are checked in, a version number is assigned and comments can be added. As a result, you have full report traceability of changes and the ability to compare, promote and restore versions as well.
Certain organizations can be more demanding than others. For example, for the US Treasury, we put in place the possibility to implement validation workflows: before reports or universes are promoted between environments, they need to be approved by a given user.
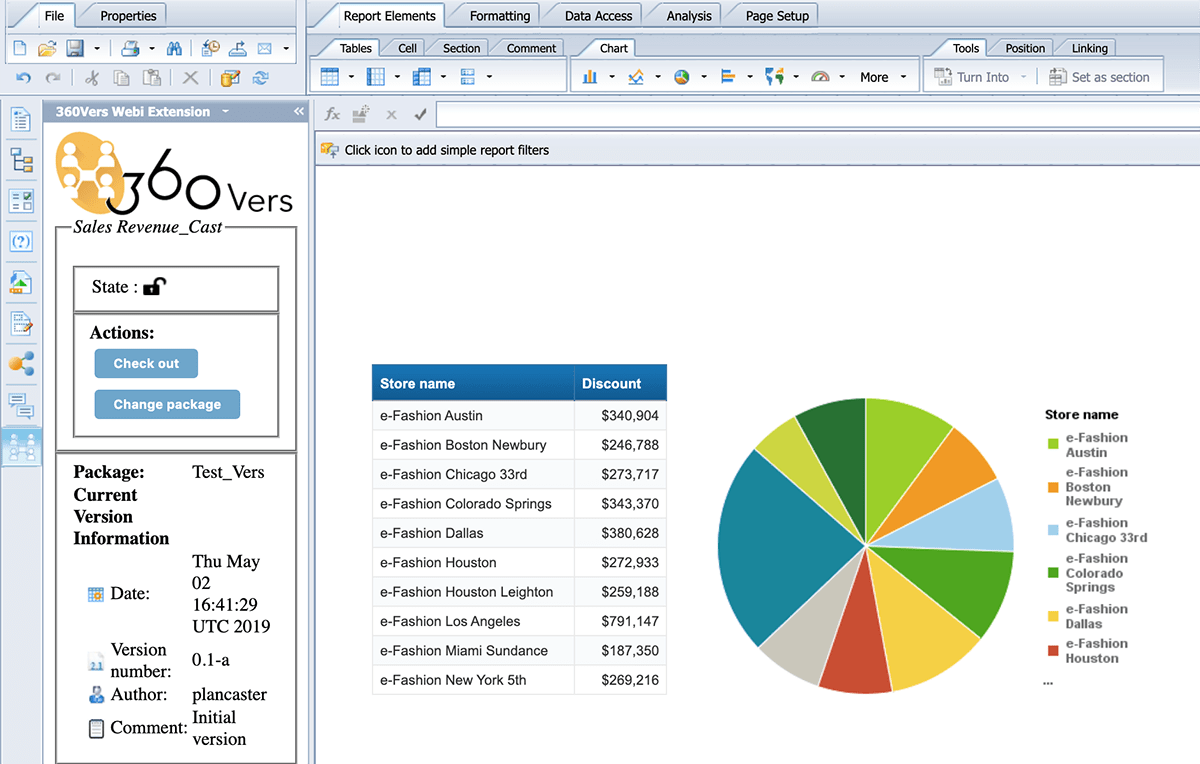
Screenshot from 360Vers extension for Business Objects Security in Version Management
Secure your schedulings and publications
Securing access to your resources at the database level, then at the repository level is great. Making sure to trace security changes and document changes is great as well. But if you don’t secure your publications, you are potentially creating a security breach.
A customer of ours realized that they were incidentally scheduling and bursting sales data to the wrong customers!
It is always better to secure bursted reports with passwords(if you can remember passwords that is 😉)!
Current state in Business Objects: You cannot secure that output format of your scheduled/bursted document with a password, whether it be a PDF or an Excel, thus making it ungoverned content.
360Suite Solutions: Don’t fret, 360Suite offers the ability to secure your bursted reports with passwords!
Conclusion
Business Objects Security is very complex as typically it is used as a reporting tool capturing data from multiple sources and delivering it to dozens of users within your organization. With common sense, basic knowledge and proper tools, it is very easy to have a secured deployment and answers to the W’s: Who, When, What, Where and Why. SAP BusinessObjects offers a lot of granularity in terms of security which can make it complicated to manage, but at the same time, it makes it one of the most secure BI platforms on the market.
Want to scan your Business Objects Security and detect your potential risks? Our experts are here to help you.